
Beginner’s Guide to Cybersecurity: How to Protect Yourself Online

In today’s digital world, learning how to protect yourself online isn’t optional—it’s essential. Every day, cybercriminals target millions of people through data breaches, phishing scams, and malware attacks. The good news? You don’t need to be a tech expert to stay safe. This beginner’s guide to cybersecurity will show you simple, proven methods to secure your digital life and protect your personal information from online threats.
1. Create Strong Passwords and Use Password Managers
Your passwords are the first line of defense against cyber attacks. Weak passwords make you an easy target for hackers who use automated tools to crack simple combinations.
How to Create Strong Passwords
A strong password should be at least 12 characters long and include uppercase letters, lowercase letters, numbers, and special symbols. Avoid using personal information like birthdays, pet names, or common dictionary words.
Instead of “password123,” create something like “Mountain$Coffee!2024” or use passphrases like “Purple-Elephant-Dances-92!”
Why You Need a Password Manager
Never use the same password for multiple accounts. If hackers breach one account, they’ll try that password on your other services. Password managers like Bitwarden, LastPass, or 1Password solve this problem by generating and storing unique passwords for every account. You only need to remember one master password.
Password Security Best Practices
Change passwords immediately if a service reports a data breach. Use password managers to identify weak or reused passwords. Enable password alerts to notify you of potential security issues. Store backup codes in a secure location separate from your password manager.
2. Enable Two-Factor Authentication for Online Security
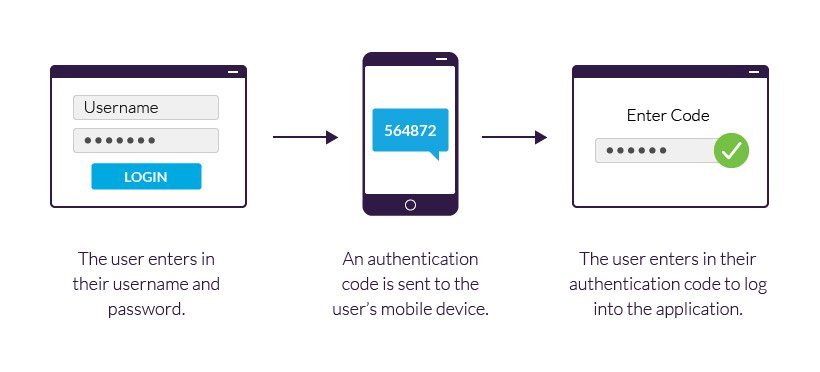
Two-factor authentication (2FA) adds a crucial second layer of protection to your accounts. Even if hackers steal your password, they can’t access your account without the second authentication factor.
How Two-Factor Authentication Works
2FA requires something you know (your password) plus something you have (your phone or a security key). When you log in, you’ll enter your password and then provide a temporary code from your phone or authenticator app.
Setting Up Two-Factor Authentication
Enable 2FA on your most critical accounts first: email, online banking, social media, and work accounts. Most services offer 2FA in their security or privacy settings. Look for terms like “Two-Step Verification” or “Multi-Factor Authentication.”
Choose authenticator apps like Google Authenticator or Microsoft Authenticator over SMS text messages when possible, as they’re more secure against SIM swapping attacks.
2FA Best Practices
Save backup codes in a secure location in case you lose access to your phone. Use multiple authentication methods when available. Consider hardware security keys for your most sensitive accounts. Never share authentication codes with anyone.
3. Recognize Phishing Scams and Email Security Threats
Phishing attacks are one of the most common ways cybercriminals steal personal information. These deceptive emails, texts, and websites trick you into revealing passwords, credit card numbers, or other sensitive data.
Common Phishing Red Flags
Watch for urgent messages claiming your account will be suspended, generic greetings like “Dear Customer” instead of your name, spelling and grammar errors in official-looking emails, suspicious email addresses that don’t match the claimed sender, and requests for personal information via email or text.
How to Verify Legitimate Messages
Don’t click links in suspicious emails. Instead, go directly to the official website by typing the URL in your browser. Contact the company directly using official contact information to verify any urgent requests. Check the sender’s email address carefully—scammers often use addresses that look similar to legitimate ones.
Email Security Best Practices
Keep your email software updated with the latest security patches. Use spam filters and enable phishing protection in your email client. Be cautious with email attachments, especially from unknown senders. Report phishing attempts to help protect others.
4. Practice Safe Internet Browsing and Software Updates

Safe browsing habits and keeping your software updated are essential for protecting yourself from malware, viruses, and other online threats.
Secure Website Identification
Always look for “https://” in the web address, especially when entering personal information. The “s” stands for secure, and most browsers display a lock icon next to secure sites. Avoid entering sensitive information on sites that only use “http://”.
Software Update Importance
Keep your operating system, web browser, and all software applications updated. These updates often include critical security patches that protect against newly discovered vulnerabilities. Enable automatic updates whenever possible to ensure you’re always protected.
Safe Download Practices
Only download software from official sources like app stores or the software developer’s official website. Avoid clicking download buttons in pop-up ads or on suspicious websites. Scan downloaded files with antivirus software before opening them.
Browser Security Settings
Use reputable browsers like Chrome, Firefox, or Safari with security features enabled. Install ad blockers to prevent malicious advertisements. Enable pop-up blockers and disable auto-play for media content. Clear your browsing data regularly to remove tracking cookies.
5. Secure Your Personal Data and Financial Information Online

Protecting your personal and financial data requires special attention, as this information is highly valuable to cybercriminals and can cause significant damage if compromised.
Online Banking and Shopping Security
Use credit cards instead of debit cards for online purchases, as they offer better fraud protection. Shop only on secure, reputable websites with verified SSL certificates. Monitor your bank and credit card statements regularly for unauthorized transactions. Set up account alerts for unusual activity.
Social Media Privacy Protection
Review and adjust privacy settings on all social media platforms to limit who can see your personal information. Avoid sharing location data, vacation plans, or personal details that could be used for identity theft. Be cautious about accepting friend requests from unknown people.
Data Backup and Recovery
Regularly back up important files to external drives or cloud storage services. Use reputable cloud providers with strong encryption and security measures. Test your backups periodically to ensure they work properly. Keep multiple backup copies in different locations.
Identity Protection Measures
Monitor your credit reports regularly for suspicious activity. Consider freezing your credit if you’re not actively applying for loans or credit cards. Use identity monitoring services to alert you of potential fraud. Never share your Social Security number unless absolutely necessary and with trusted organizations.
Wi-Fi and Network Security
Avoid using public Wi-Fi for sensitive activities like online banking or shopping. If you must use public Wi-Fi, consider using a VPN to encrypt your connection. Secure your home Wi-Fi network with WPA3 encryption and a strong password. Change default router passwords and keep firmware updated.
Take Action: Your Next Steps to Better Online Security
Cybersecurity doesn’t have to be overwhelming. Start with these three immediate actions: install a reputable password manager and create strong, unique passwords for your most important accounts; enable two-factor authentication on your email, banking, and social media accounts; and update all your software and enable automatic updates.
Remember, you don’t need to implement everything at once. Focus on building good security habits gradually, and you’ll significantly improve your protection against cyber threats. Stay informed about new security threats and continue learning about cybersecurity best practices to keep your digital life safe and secure.














Post Comment